In our previous blog, we have covered about setup federation farm. AD FS is a standards-based service that allows the secure sharing of identity information between trusted business partners (known as a federation) across an extranet.
Most people will deploy Web Application Proxy to avoid publish ADFS to the Internet. Yes, this is one of the way. But we want to be more secure !
In order to achieve more secure environment, we can deploy MFA in our on-premise environment. Check out on our deployment scenario:
[ Scenario]
- Domain Controller
- ADFS Farm
- Application Proxy
- Azure Subscription
- Office365 (for testing app)
[ Before setup scenario ]
User login to portal.office.com with valid username. Page will redirect to ADFS server page and request to enter valid password. At this moment, communication has reached to Web Application Proxy and ADFS. ADFS will verify the username and password where user account is reside in the domain controller.
After authenticated, it will redirect to Office365 portal without 2nd level authentication.
[ Configuration for MFA]
Go to Azure Management Portal and create a new Multi Factor Auth provider under Active Directory Section. You can enable either per user based or per authentication.
Click on Manage, download the MFA Server and install on the protected server.
Install the MFA Server and use the Activation Credential (valid for every 10 minute). Skip any configuration wizard.
Click on ADFS and configure the settings that you require and click Install ADFS Adapter. After installation of ADFS Adapter, you’re require to restart the server.
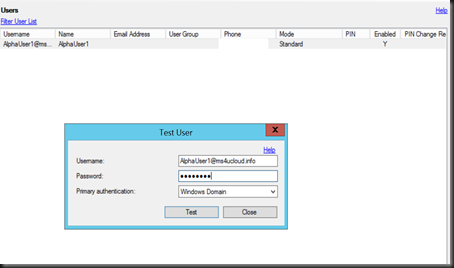
Next step is Add User. Click on Users and Import from Active Directory. For our test purpose, we select alphauser@ms4ucloud.info. By default, user will be disable if no phone number is enter.
Just edit the user, enter phone number and tick enable
Perform a test by entering a valid password. You will receive a call. Just press # to confirm.
We are still not yet complete.Open Powershell on ADFS server and execute
| .\Register-MultiFactorAuthenticationAdfsAdapter.ps1 |
Restart the server and modify the global policy from ADFS Snap-in. Go to Authentication Policies | Edit Global Multi Factor Authentication.
Set a policy. We just enable MFA for alphauser login from Extranet either he is using unregistered or registered devices.
[Verification]
Time for verification and make sure it is working as expected.
This round rather than redirect to Office365 after key in credential, the system will prompt user to 2nd level authentication. You will receive a call. Just press # to confirm and enter additional security question.
Once completed, you will able to access Office365 portal.
In this article, we have secure our environment by enabling MFA when customer using Active Directory Federation Server with Office365.