In our previous post, we have explore on how to configure multi-site vpn in Azure for our domain controller. Next we are going look on how to extend our data center network by connecting an Azure virtual network (Vnet) to another Azure virtual network. Both virtual network is going to connect to a secure tunnel using IpSec/IKE.
These connectivity is important when you would like to setup
- Geo-redundancy via same region / different region without going over internet facing endpoint
- Connect workload from different Azure subscription
- Connect same region or different region
- Setup a DR to another region. Example:- You have setup VM infrastructure at Southeast Asia Region – datacenter located in Singapore (SG). For redundancy we can setup geo-replication storage which replicate entire content to Hong Kong(HK) data center. But these implementation only contained content and we are still require to re-create cloud configuration and remap to our VM when disaster occur. Process of re-creating cloud configuration require more effort and downtime. Therefore one way to reduce downtime is setup another similar infrastructure in another region. That’s what this post is all about.
Let chec out our setup environment
- Multi-site vpn connection between HQ and Branch. We had configured this our previous post. So we are going to skip these step.
- Two different Azure subscription
- Affinity Group 1- Southeast Asia (SG Datacenter)
- Affinity Group 2 – East Asia (HK Datacenter)
| Region | Local Network | Virtual Network | VPN Gateway |
| Southeast Asia Region | 10.0.0.0/24 | Ms4U-AzureVnet | 138.91.33.133 [Created from our previous post] |
| East Asia Region | 172.160.0.0/24 | DR-Vnet | [Will determine later] |
Since we have completed our 1st region on our previous post, let move on to 2nd region.
- Create Affinity Group
Settings –> Affinity Group –> +ADD –> “MS4U-DR (located in East Asia Region)
- Create new storage
+NEW –> Data Services –> Storage –> Quick Create
- Create new Virtual network
+New –> Network Services –> Virtual Network –> Custom Create
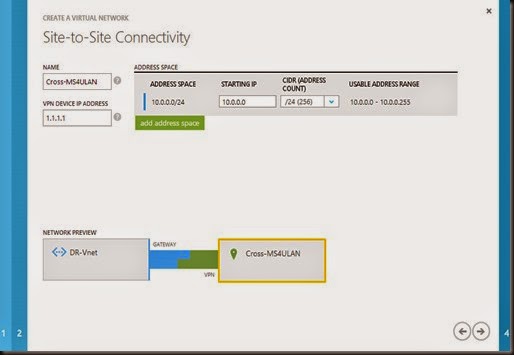
Define name “DR-Vnet”
Select “Configure site to site vpn”
Define 1st region virtual network address and temporary VPN Gateway IP
- 10.0.0.0/24 (virtual network)
- 1.1.1.1 (VPN gateway- we will modify later)
Define 2nd Region virtual network. Here we will be using 172.16.0.0/23 subnet. Make sure no overlap subnet on both virtual network.
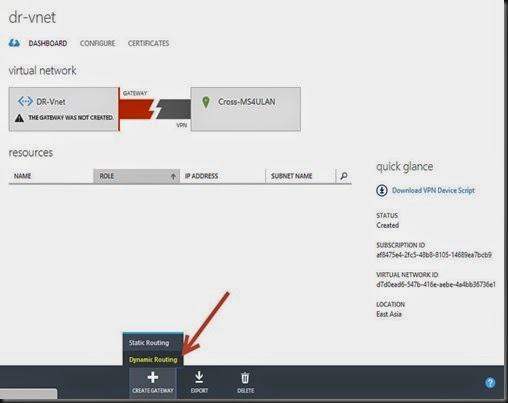
- Create VPN Gateway for 2nd virtual network – “DR-VNET”
Network –> DR-Vnet –> Dashboard –> Create Gateway –> Dynamic Routing
NOTE:- Creating vpn gateway will took around 20 minute.
- While waiting, check the 1st virtual network VPN Gateway.Jot down the IP
- Go to Networks –> Local Network –> Edit “Cross-MS4ULAN” VPN Gateway. Replace 1.1.1.1 with the correct VPN Gateway which we have capture from previous step
Now we have setup the 2nd virtual network. Let modify the 1st virtual network by export 1st virtual network configuration. To do so click on EXPORT.
Modify the entry to include 2nd virtual network (highlighted in green)
| <NetworkConfiguration xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://schemas.microsoft.com/ServiceHosting/2011/07/NetworkConfiguration"> |
Then import the new network configuration
+NEW –> Network Services –> Virtual Network –> Import Configuration
Verify that new virtual network has added- “Cross-DR”
Before we connect both network, remember to change both shared key to the same key so these virtual network can communicate with each others.
On 1st virtual network
| Set-AzureVnetGatewayKey –VnetName MS4U-AzureVnet –LocalNetworkSiteName Cross-DR –Sharedkey MS4UKEY |
On 2nd virtual network
| Set-AzureVnetGatewayKey –VnetName DR-Vnet -LocalNetworkSiteName Cross-MS4ULAN –Sharedkey MS4UKEY |
Once you’ve change the key, click on CONNECT
Connection on 2nd virtual network is “Connected”
On the 1st virtual network is also “Connected”
Once connection has established, virtual machine from 1st region was able to ping to 2nd region. We have successfully connect vNet to another vNet.
Our above configuration was guided from the documentation published by Microsoft Azure. To know more, please click here.