In our previous post, we have talked on building RRAS to connecting two subnet and network address translation. If you’re interested, feel free to check out here.
Next, we are going to embark a journey to Hybrid Cloud by connecting to Microsoft Azure by using RRAS.
[ Scenario]
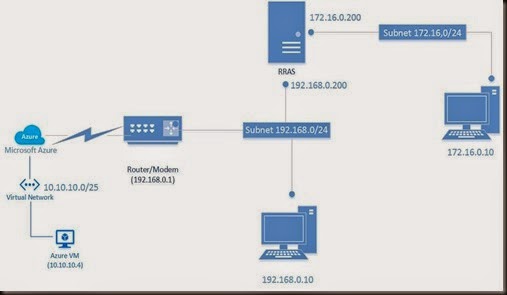
Continue from previous post setup. We are changing it to include demand-dial.
[ Before – on Azure]
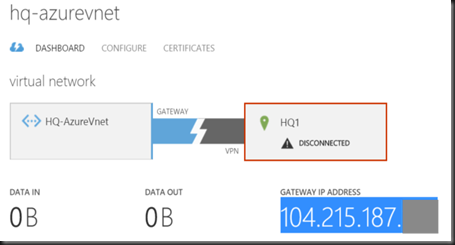
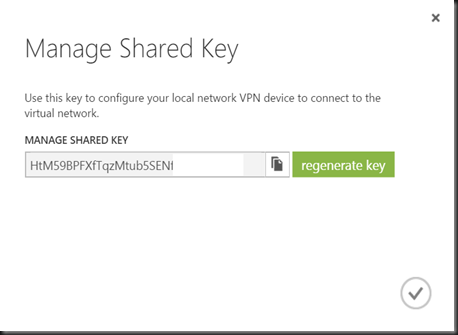
Create Virtual Network and create dynamic VPN Gateway. Take note and Gateway IP Address and Pre-Shared Key
[ Configuration on RRAS]
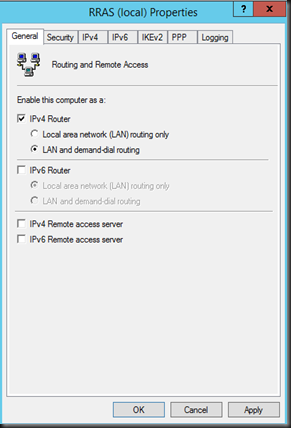
1. Modify to include demand dial. Set LAN and demand dial routing on Ipv4 router
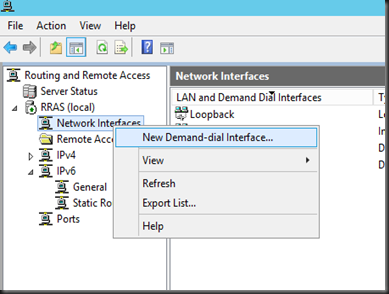
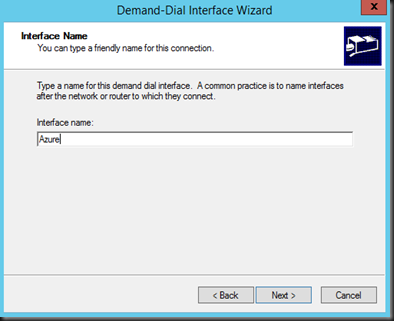
2. Add a demand dial interface and modify accordingly
3. Connection type set to VPN
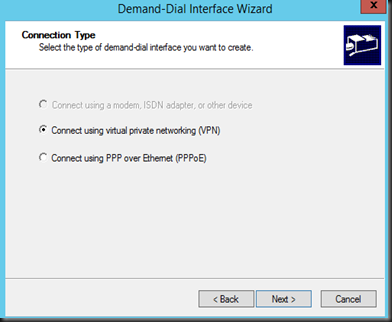
4. VPN Connection set to use IKE v2
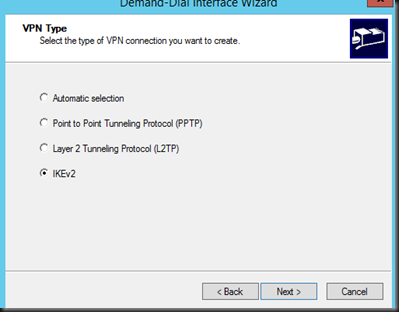
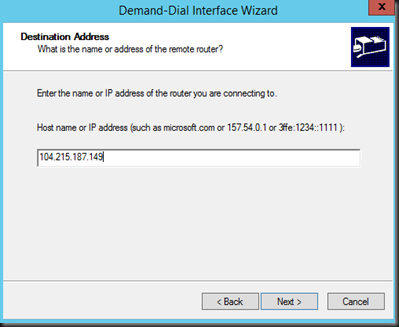
5. Enter Azure VPN Gateway IP that you have created on previous step
6. Tick Route IP Packet on this interface and enter destination route detail (enter Azure virtual network information)
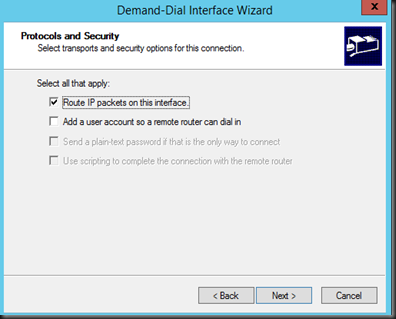
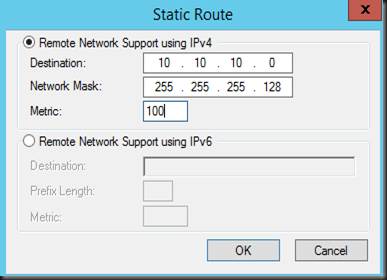
7. On Credential, leave it empty. We are going to set pre-shared key later.
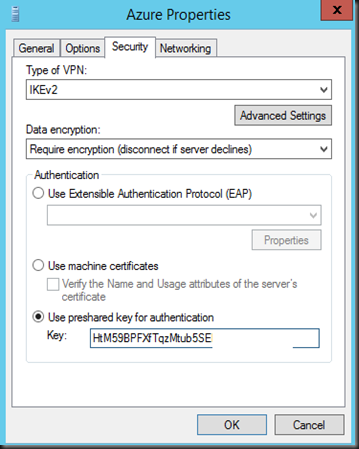
8. Modify the demand dial interface. Go to security tab and set to use pre-shared key
[ Verification]
- Try establish connection from RRAS
- Connect on Azure Portal
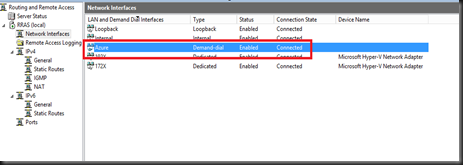
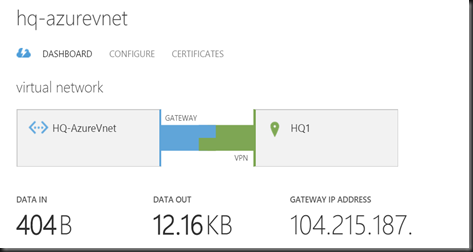
Yeah! Both reported connected
To make sure that both side can access, perform ping test and tracert.
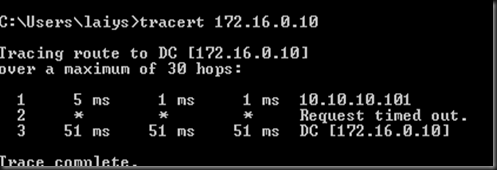
[ Test result]
From Azure VM to on-prem DC VM
From on-prem DC VM to Azure VM
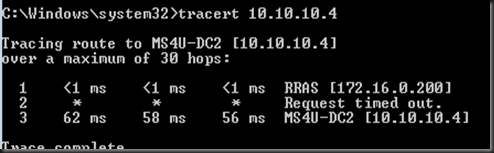
Easy right! That’s concluded our configuration to establish site to site vpn to Microsoft Azure by using RRAS.