Not long ago I’ve met several customers and we had a great discussion on setup Windows Azure. Most of them would like to put Active Directory in Windows Azure but it has a limitation that you only can setup one connection from your on-premise to Azure. What happen when you have multiple branch environment and would like to connect to same virtual network on Azure?
Too bad it won’t work till recently TechEd NA 2014. Guess what? Microsoft make an announcement to released this feature called “Multi-site VPN”.
Something great and excited to deploy. Here is my setup environment:-
Datacenter
HQ MS4U
- External Public IP
- Firewall that support dynamic routing VPN / route based VPN
- MS4ULAN Site – 192.168.20.0/24 Subnet
Branch MS4U
- External Public IP
- Firewall that support dynamic routing VPN /route based VPN
- Site2MS4ULAN Site – 192.168.30.0/24 Subnet
Azure (Region SEA)
- Virtual Network
- Infra Subnet – 10.0.0.0/27
- Web Subnet – 10.0.1.0/27
- Database Subnet – 10.0.2.0/27
Virtual Network Gateway – must configure to use dynamic routing
Note:-
- No overlap ip between HQ and branch local network
- Primary DC (holding FSMO roles) located at HQ MS4U
Step 1:-
- Configure Site to Site VPN to HQ MS4U using Azure Management Portal
- Make sure site to site vpn is establish between Azure VPN Gateway with HQ MS4U Firewall
- Setup an additional domain controller in Windows Azure. Click here to learn on how to setup DC. The guide is refer to Read Only Domain Controller (RODC) but the step is identical. (Just don’t select RODC role)
Step 2:-
- Export network configuration on the virtual network that you have created on Step 1
Network | (your virtual network) | Export | Save as NetworkConfig.xml
- Edit the network configuration using notepad. Modify to include 2nd site information (highlighted in green)
| <NetworkConfiguration xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://schemas.microsoft.com/ServiceHosting/2011/07/NetworkConfiguration"> |
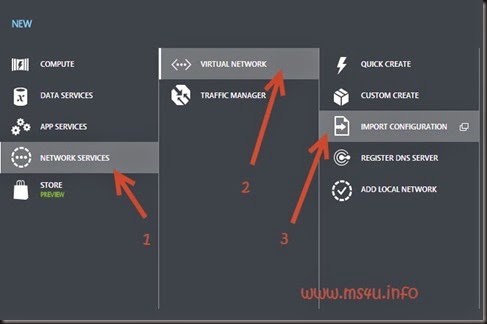
- Save it and import to Azure using Azure Management Portal.
- + New | Network Services | Virtual Network | Import Configuration.
Note:-
- From now onward, you need to use network configuration to configure settings. Once you import the settings, you will not able to change from UI.
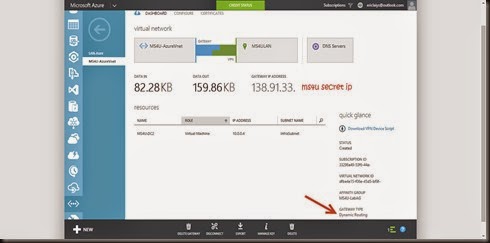
Before import:-
After import the new configuration, the virtual network will display the following information. You need to use Windows Powershell or REST API.
2 tunnel created
- MS4ULAN Site – for HQ MS4U
- Site2MS4ULAN Site – for branch MS4U
Step 3:-
- Download Windows Azure Powershell from here.
- Connect to your subscription
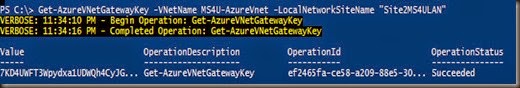
- Get your pre-shared key for the VPN tunnel
| Get-AzureVnetGatewayKey –VNetName (site to site vpn virtual network) –LocalNetworkSiteName (site name) |
Check the multi site tunnel using Get-AzureVnetConnection
Step 4:-
- Configure branch –MS4U firewall to setup site to site vpn to same VPN gateway in Azure
- Sorry. No VPN script that you can download. This option is no longer available once you import the network configuration to allow multisite.
- You must familiar on how to setup site to site VPN on firewall
- Enter the pre-shared key that you’ve gathered in Step 3
Step 5:-
You are almost there…
- On the Azure Management Portal, you will be able to see both firewall has successful connected to VPN gateway in Azure and we now have “Multi-site VPN”
- On branch MS4U, you can proceed to setup another an additional domain controller which pointing to Windows Azure DC.
That’s all for now. We will do more further test and post it in our next article.
Stay tuned!