In this article, we will look on how to configure Port ACL (Access Control List) in Hyper-V to provide additional security in the virtualization infrastructure. If you are familiar with Cisco switch, probably you know the function of ACL. Both is similar and the purpose is to filter ingress and egress traffic based on conditions specified in the ACL.
By default, when create a virtual network adapter there is no ACL on it.
Command to use on configure Port ACL:-
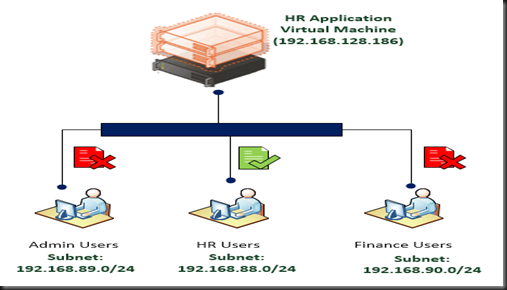
Scenario on my test environment:-
- Only allow HR User (reside in subnet 192.168.88.0/24) to access HR Virtual machine (name: VM1).
- Prevent Subnet 192.168.89.0/24 and 192.168.90.0/24 from accessing HR VM
Note:- above scenario is just one of the sample scenario.
To configure port ACL, you need to use Powershell. No GUI !
Description on how to to add Port ACL:-
Command to use: Add-VMNetworkAdapterACL
- Specify the VM name to apply the ACL
- Remote IP Address (Ipv4 or Ipv6) or Remote Mac Address
- Direction – Inbound traffic, OutBound traffic, Both (Inbound & Outbound)
- Action – Allow traffic, Deny traffic, Meter – to measure traffic
| Add-VMNetworkAdapterACL –VMName VM1 –RemoteIPAddress 192.168.88.0/24 –Direction Both –Action Allow Add-VMNetworkAdapterACL –VMName VM1 –RemoteIPAddress 192.168.89.0/24 –Direction Both –Action Deny Add-VMNetworkAdapterACL –VMName VM1 –RemoteIPAddress 192.168.90.0/24 –Direction Both –Action Deny |
To view the ACL result
| Get-VMNetworkAdapterACL |
To remove Port ACL (one ACL at a time):-
Command to use: Remove-VMNetworkAdapterACL
| Remove-VMNetworkAdapterACL –VMName VM1 –RemoteIPAddress 192.168.88.0/24 –Direction Both –Action Allow Remove-VMNetworkAdapterACL –VMName VM1 –RemoteIPAddress 192.168.89.0/24 –Direction Both –Action Deny Remove-VMNetworkAdapterACL –VMName VM1 –RemoteIPAddress 192.168.90.0/24 –Direction Both –Action Deny |
To remove entire Port ACL that apply to VM1:-
| Get-VMNetworkAdapterACL VM1 | Remove-VMNetworkAdapterACL |