There are three way of connecting resources on private cloud to Windows Azure
- Site to Site VPN
- Point to Site VPN
- Express Route (new- Feb 2014)
Site to site VPN is relies on a IPSec VPN appliance to be deployed at the edge of your network for connectivity. This method allow any computers on your premises to connect any virtual machine / PaaS instance within the virtual network.
Next is Point to Site VPN. It work exactly like VPN client. You have to install a VPN client configuration package that enable your computer to connect to any virtual machine / PaaS within the virtual network. Point-to-site connectivity is over SSTP (Secure Sockets Tunneling Protocol) and support up to 250 VPN client.
Lastly Express Route is a dedicated private and high throughput network connectivity and guaranteed Network Qos to ensure faster speed, low network latency and complete network isolation. Check out here.
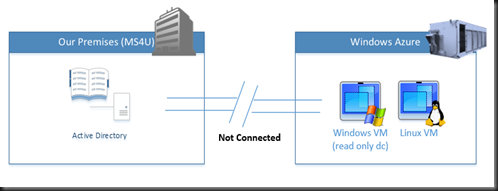
In today post, we are going to talk about Point to Site VPN so we can connect Active Directory at our premise to a virtual machine holding read only domain-controller roles. This allow us to have a non writable active directory running at Windows Azure to use by any virtual machine. This is just an example that we are trying to simulate on our testing environment and just to let primary domain controller to communicate with the new VM.
It look like our scenario is not connected. New VM has created for read only domain controller but without the connection to our premises, we cannot replicate the active directory object. To do so, you need to
a) Configure Virtual Network
b) Create self signed root certificate
c) Deploy VPN Client Configuration
Configuration – Configure Virtual Network
Click +New | Network Services | Virtual Network | Custom Create
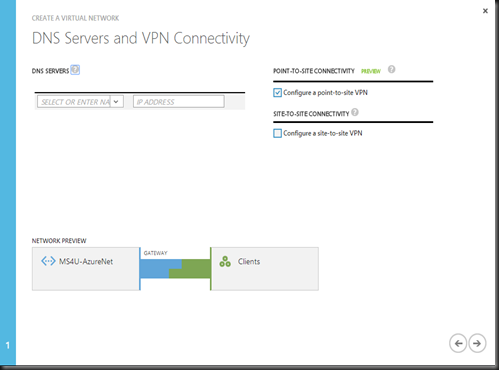
Enter Virtual Network Details
Make sure to select “Configure a point to site VPN”
Configure Virtual Network Address Space on your virtual network
Once you have complete the wizard, you need to start create a dynamic routing gateway and this would take around 10 –20 min. Click on your virtual network that you’ve created on previous steps. Click + Create Gateway
After 20 minutes, this is how it look like . The system require us to proceed to next step.
Configuration – Create Self Signed Root Certificate
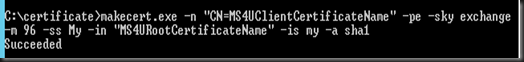
1. Download and Install Visual Studio Express 2013 for Windows Desktop to create self signed root certificate. In our example, we have created self signed root certificate and client certificate.
Create Self Signed Root Certificate
Create Client Certificate. Generate client certificate from the root certificate that does contain the private key and install on each client computer that you want to connect to VPN.
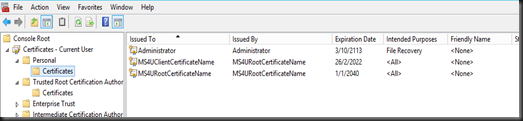
Install the self signed root certificate and client certificate on your primary domain controller. You can verify by using MMC Snap-in. Both certificates are listed there.
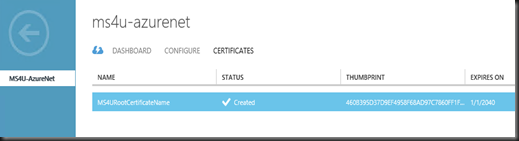
2. Upload root certificate .cer file (without private key) to Management Portal
We use SSTP (Secure Sockets Tunneling Protocol) to tunnel through firewalls. This tunnel will appear as a HTTPs connection.
Configuration – VPN Client Configuration
Certificate are uploaded and installed, you can download and install VPN client package on your primary domain controller.
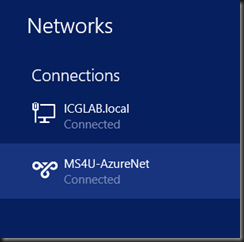
On your network connection, a connection has created. Right click and select Connect
Click Connect to establish the connection.
If successful, you can view the status on the network mentioned “Connected”
To verify:- go to command prompt, type ipconfig /all.
Your domain controller will getting a virtual network ip address (10.0.0.2)
Back to Windows Azure Management Portal, refresh the dashboard. Voila! The connection is “Established”
With the connection established between our premises to Windows Azure, we can now start building read only domain controller VM at Windows Azure.
Please check on our other post: